 IBM i’s RCAC functionality offers a flexible option for securing sensitive data like social security numbers, credit card numbers, and more–without requiring complex modifications to integrated applications.
IBM i’s RCAC functionality offers a flexible option for securing sensitive data like social security numbers, credit card numbers, and more–without requiring complex modifications to integrated applications.
With IBM i’s stock toolset, however, managing RCAC settings requires a database administrator with SQL programming skills. But now, PSGi’s new Field Level Security Manager makes it much easier to manage field level access through a streamlined graphical user interface.
In this blog, we explain RCAC, how it works, and how PSGi’s new tool makes field level security easier to implement than ever before.
What is RCAC? Field Level Security in IBM i
Since version 7.2, IBM i has offered DB2 field level security capabilities called Row Column Access Control (RCAC). By obscuring sensitive data at the database level, RCAC offers a practical means for keeping data more secure without redesigning applications or creating new tables.
Prior to version 7.2, IBM i applications written in RPG only supported menu or option-level security. This means that users can be prohibited from accessing a given menu or function, but once a user has access to part of the system, all the data within that system is fully accessible. This same logic applies to the database layer: a user has access to either a full table, with all of the data it contains, or no access at all.
RCAC provides businesses with the ability to secure data on a more granular basis, to the level of specific characters within specific rows and columns. Even if a user has access to a given table, they will only see a redacted entry (such as asterisks or 9’s) in protected fields. Provided through SQL rules applied directly at the database layer, field level protection is applied to queries from both integrated IBM i applications and external systems.
Flexible Security: No Modifications Required for Integrated Applications
In addition to general cybersecurity concerns, regulations like GDPR and CCPA will only add to the growing pressure to secure sensitive data. Many longstanding business applications were not built to address today’s data security requirements and re-architecting applications to reflect contemporary data security practices is often uneconomical. In this context, RCAC provides a flexible solution. By protecting data at the field level, sensitive information can be hidden from users who do not require it for their job function. But, critically, restructuring user access at an application level is not required: if a user queries a protected field, they receive a redacted response, not an error message.
This flexibility can be valuable across a broad range of job functions. For example, RCAC can readily be configured to allow shipping operators to access customer order data for fulfillment purposes, without granting them access to sensitive information like order pricing information. Without field level security, keeping this data safe would require creating an entirely new table and modifying the relevant applications to use the new table. With RCAC, this process is dramatically simplified, without upending a complex series of permissions that potentially business-critical workflows for sales, accounting, and customer support depend on.
In its base implementation in IBM i, however, configuring RCAC functionality requires a database administrator, even for routine user access changes or rule modifications. PSGi wanted to offer users the ability to change field level permissions without a costly DBA resource or labor-intensive programming. So we built an application that does just that.
Introducing PSGi’s Field Level Security Manager for IBM i
PSGi’s Field Level Security Manager simplifies the process of setting rules for displaying redacted data to users based on customizable field level permissions. While it makes use of IBM i’s RCAC functionality, this definitional software makes it far easier for non-technical users to set and modify rules and permissions.
To use the tool, a user only needs to be granted DB Security Admin Rights, and may then login using their AS/400 credentials.

After logging in, all previously created rules are readily viewable through a streamlined interface. Entries are sortable.
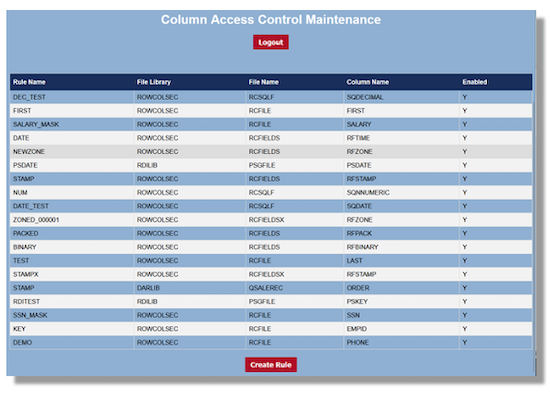
Each rule can be inspected with a simple click. From here, authorized users can be easily added or removed. field level rules are fully customizable. Users can select the number of decimal places at which a value will be obscured, the characters used to redact data, and more. One of the only key restrictions is that the character used to redact data must match the relevant field type. For example, a numerical value must be obscured using all 9’s rather than asterisks.
New rules can be created using the same interface. All required SQL coding is performed automatically “under the hood.”
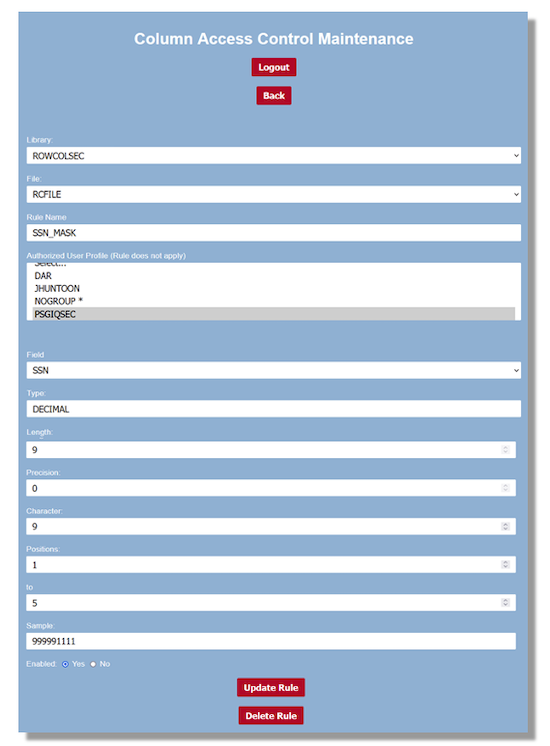
Without PSGi’s software, all of these changes would require a database administrator to write or modify SQL code! By making RCAC configuration accessible through an intuitive graphical interface, this solution makes it easier to update field level security on the fly without the need to wait for a specialized resource. Even for a skilled database programmer, this application is far less labor-intensive than directly programming rule changes.
If you are interested in learning more about Field Level Security Manager, please visit the product page found here.

